Security & Privacy
The security of home automation systems has often been overlooked, in favour of adding functionality and novel devices. In this system, security is given top priority over all other considerations. It determines the overall architecture of the system, and is an embedded feature of every aspect.
Keeping It Simple
Despite the extent of the security measures, the system remains straightforward to install, to configure, and especially to use. This is achieved by hiding the means by which security is achieved from the user, except where their involvement is unavoidable.
One of the main advantages of this configuration, in addition to its greater security, is the prevention of any direct remote access to devices within the home automation system. In particular, personal data, such as videos and images captured on camera are stored on the hub, unless the user specifically chooses to relay them to the cloud.
More generally, the extent to which the user may want to make use of the cloud based facilities is entirely at their discretion, because the system can be configured to operate 100% locally.
The User’s Perspective
In 2016, Intel Security surveyed some 9,000 consumers in relation to home automation systems, most of whom were located in North America and Europe.
Despite the falling price of home automation in real terms, the consumers’ concerns over the security of home automation systems, and the potential invasion of their privacy have held back the growth of this market.
Over 90% of those surveyed were concerned about their personal data being hacked, and nearly 70% had worries over cybersecurity. The many instances of hacking and data misuse during the last two years have strengthened these views.
The findings of this survey are still very relevant today.
Users also want simplicity of operation, a single point of access, and a single means of authentication.
Local Operation
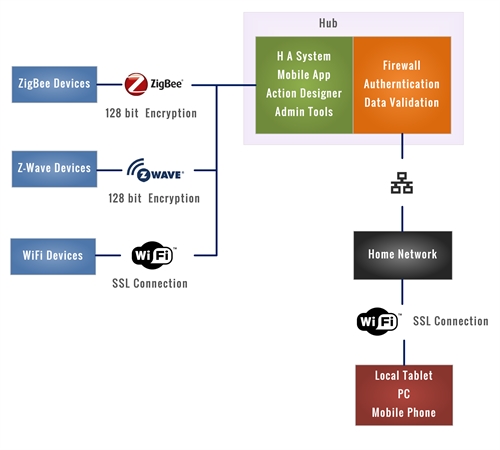
All of the devices controlled by the home automation system are connected securely to the hub through a combination of encryption and individual device identification.
The entire HA control system, including the mobile app, the action designer, and other supporting administrative tools run locally on the hub.
The hub has a direct Ethernet connection with the local home network.
All of the services running on the hub are protected by a software firewall, the authentication of all local users, and the validation of all local requests and data.
A tablet, PC, mobile phone, or other similar device can be connected locally by WiFi and the home network to the hub. The system is controlled and managed through a conventional internet browser running on the device in conjunction with a web app running on the hub. An SSL connection is used between the device and the hub.
Remote Operation
The hub firewall can be configured to permit direct communication between it and specifically identified devices for direct remote access.
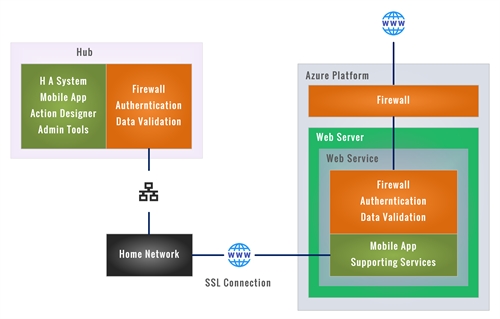
The preferred alternatively, for improved security, is for the hub firewall to be configured to only permit communication between the hub and an associated secure web server running in the cloud.
The mobile app is replicated on the web server, to which the user has access, instead of connecting directly with on the hub. The web service then acts as a request / response and data interchange between it and the hub.
The web server embodies the additional protection of the Microsoft Azure platform, including its built-in firewall. An additional firewall, running as part of the web service, further limits access to identified devices. All remote users are authenticated, and all remote requests and data are validated on the web server.
An SSL connection is employed between the hub, via the home network, and all remote devices, including the associated web server.
This approach enables the user to either:
Connect their remote mobile device to the hub, without relying on any cloud based service, or
Benefit from the higher level of security provided by the cloud based service.
The user is given the option of running a hybrid app on the web server, instead of a browser based web app. This enables data to be exchanged between the remote mobile device and the hub in the background, and independently of the normal use of the remote mobile device.
Radio Frequency Interference
The Achilles Heel
All home automation systems employ radio signals for communication between the hub and the individual devices. This is a potential security weakness, and a means of invading a person’s privacy.
Stories continue to appear in the media about these radio signals being hacked. Fortunately, the return for anyone hacking a system does not warrant the amount of effort involved, except for those homes with very high value contents, or occupied by high profile people. Even so, the articles that appear in the media continue to raises concerns amongst potential users.
The level of encryption and other security methods make these systems very robust during normal operation. The weakness occurs when their radio signals are disrupted, which often leads to devices having to be reconnected to the network, which is the Achilles heel of these systems.
Weak radio signals, low battery power, and software / firmware programming errors are the three main causes of loss of connection.
The Solution
As with any situation, prevention is better than cure, so it essential for the system to monitor, and report, on signal strength and quality, and battery levels. This forms part of the system health monitoring and self-testing, which are described elsewhere.
Software / firmware programming errors can be minimised through the use of the latest professional programming languages and best programming practice, which are described elsewhere.
When a device loses connection with the rest of the network, it has to be re-joined, which is often a semi-manual operation. A rogue device, controlled by a hacker, can also be joined to the network during this re-joining process. Having joined the network, the rogue device can then take control of the network, in place of the hub. This is not just a theoretical possibility, and it can be largely automated.
The hacker can then make changes to the device settings, one of the most concerning being the unlocking of exterior doors. As this form of hacking can be largely automated, it does not require the hacker’s full time involvement, or even their presence.
Taking control of a network in this way is not just a theoretical possibility. We have used this method to take control of the smart heating system of a major UK brand.
The best solution is for the hub to maintain a list of those devices that have been joined previously, and are still eligible to re-join, and for the user to check and confirm any devices that have joined or re-joined.