Hub Applications Software
Summary
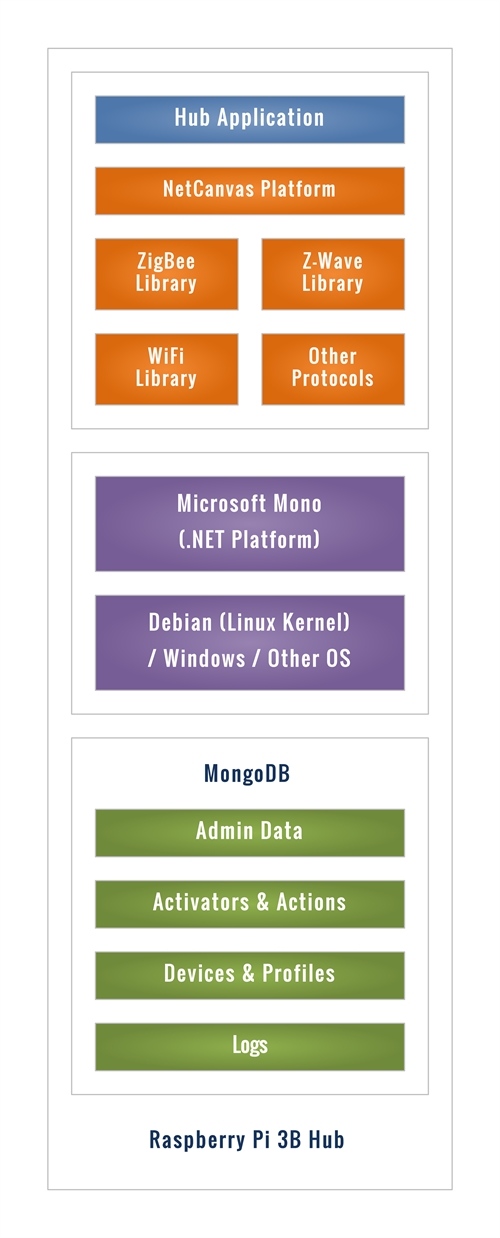
The hub application programs, which are written in Microsoft C# run on the NetCanvas platform, include everything required for the operation of the entire system. It is self-contained and does not require an Internet connection.
The user interface is provided by a mobile phone or other device connected locally by WiFi to the home network, or remotely.
Network Management
The hub software manages the radio networks that are used to communicate with the various devices.
Multiple different networks can be used, with a separate network adapter for each network. The system has been configured initially to meet the requirements of two main types of user, one in the UK, and the other in the USA.
This requires two ZigBee networks, one Z-Wave network, and one WiFi network. One ZigBee network is for the current home automation devices, and the other is for the older AlertMe and Lowes Iris devices.
There is only one Z-Wave protocol, but it operates at different radio frequencies, depending on whether the installation is in the UK or the USA.
The hub software controls each of these networks directly, and without the use of bridges or other interfacing devices.
While this described configuration is only using two ZigBee networks and one Z-Wave network, the control system has no limit on the number of ZigBee or Z-Wave networks it can support.
Device Management
The hub software communicates with and manages each of the devices attached to each of the networks. This extends down to the level of endpoints, clusters, and attributes. It controls each device individually, and without reliance on any third party software in any form.
The control of the devices, and the data obtained from them includes features that are not normally advertised by the device manufacturer, and are probably known only to them. For example, a motion sensor might also measure the local temperature and light level, and report these back to the hub.
Cloud Communications
The hub can communicate with a secure web service running in the cloud, which is in the form of a data synchronization between the hub and the web service. This is under the full control of the hub software, so it is able to prevent any interference with system originating from the Internet.
The user can enable remote access either directly via the hub, or via a secure web service running in the cloud, which provides an additional level of security.
The cloud is also accessed by the hub for updates, and for backing up the hub data, both of which are optional, and under the control of the user.
Self-Monitoring
The hub software employs self-monitoring to assure both the security of the system and its health.
Each device is controlled individually by the hub software, so that the entire operation of the system can be monitored. This includes feedback from actuators, such as smart plugs, to ensure that they have responded correctly to commands issued by the control system.
The system also includes full monitoring and reporting on the signal quality and strength for each device, and the battery level of each battery powered device.
Activators & Actions
Actions are performed by the control system in response to user commands. These are relayed to the actions by activators, which provide the user interface.
This may be no more than switching a smart plug on or off in response to the user tapping a button on the mobile phone. At the other extreme, it may be to secure the entire property by locking the external doors, activating motion sensors, and then reacting automatically to a detected intruder.
The hub software provides the user with the on-screen tools for controlling the everyday use of the control system via the activators. The actions, which are invoked by activators, and control the operation of the control system.
The creation and maintenance of these activators and actions are handled separately from their normal everyday use. The hub software includes an activator designer and action designer for this purpose. These enable users to create their own actions without the need for any programming or pseudo programming skills.
Local & Remote User Access
The hub software includes a mobile app, through which the user is able to control both the normal everyday use of the system, and its management.
The user’s device, which can be a phone or a tablet, or even a laptop or desktop computer, accesses the hub software via the local home WiFi. This is a web app, which only requires the use of a normal internet browser on the user’s device, so the user does not need to download the app from an App Store.
The hub operates stand-alone, and without any reliance on the cloud or an internet connection. All of the commands received by the hub, including those from the local home network, are under the full control of the hub software, so it is able to prevent any unauthorised access to the system.
Users can optionally enable remote access directly to the hub, so that they can control the everyday use of the system when away from home, and without any reliance on any cloud software. The also has the option of controlling the system via the supporting cloud services, which provides an additional level of security.
User Management
As with all of our secure online applications, strict rules are applied to the rights and roles of each user or user group. This prevents anyone from accessing any aspect for which they are not authorized, and limits the access of authorized users according to their rights.
In this application, users only have access to aspects and data that is specific to their particular account (home), as identified by the hub.
There are two main user groups for each account, namely owners and other users. Owners have full access to the entire system in their home. Individual users have control over their own environment, which might include their room and some areas to which all of the members have access within the home. The owner still has overriding control of the entire home.
One or more users can be registered to use each hub. Each these users can access their hub directly, or via the hub’s secure area within the cloud.
These secure hub areas within the cloud also contain a copy of the hub settings, which can be backed up from the hub either automatically or manually, at the owner’s discretion, together with other hub specific data.